Our News Blog
Featured Posts
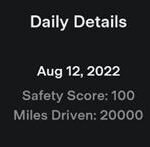
Tesla Hacking: Part 2 – Spoofing Tesla Insurance (Safety Score) Telemetry Data
Shortly after obtaining root access on a Tesla Model 3,…
Tesla Hacking: Part 1 – Obtaining Root on a Tesla Model 3 with Persistent Access
We at SourceHat enjoy Tesla’s vehicles. They become more enjoyable,…
Avoiding Losses In DeFi Staking – Part 1: Tracking Deposits And Rewards
In the ever-evolving realm of decentralized finance (DeFi), the spotlight…
Latest Blog Posts
Tesla Hacking: Part 2 – Spoofing Tesla Insurance (Safety Score) Telemetry Data
Shortly after obtaining root access on a Tesla Model 3,…
Tesla Hacking: Part 1 – Obtaining Root on a Tesla Model 3 with Persistent Access
We at SourceHat enjoy Tesla’s vehicles. They become more enjoyable,…
Avoiding Losses In DeFi Staking – Part 1: Tracking Deposits And Rewards
In the ever-evolving realm of decentralized finance (DeFi), the spotlight…
Secure Your Blockchain Project with a Professional Audit
Request a comprehensive blockchain audit from Chainsfoundations and ensure the success of your project.